Search for Certificates on Windows Systems
Nine Inch Nails - Broken
Here are a lot of words about what's essentially a one-line CMD + Powershell script...
I've recently run into a situation where a trusted root certificate authority certificate was missing from several Windows systems in multiple locations and domains. This was causing an issue with automation which reached out to a site which had a certificate signed by that CA. I can see a good use case for this if an organization has their own CA and needs to verify that all endpoints have that CA certificate in their trust store for example.
It turns out I couldn't quickly find a way to deal with this with a CMD based tool, but I did find a powershell command to list installed certificates which worked great, so I wrapped it in some ugly FOR loops and that was about it.
A couple of pre-reqs:
For example, here is a Microsoft Root CA Certificate Thumbprint
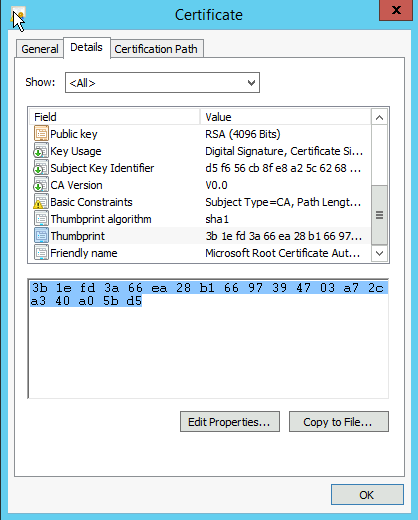
If you manually browse for the certificate on a known-good machine as above, you can get the thumbprint here. You need to take that string and uppercase all the letters and remove any whitespace, so it will look like "3B1EFD3A66EA28B16697394703A72CA340A05BD5"
An easy way to change the thumbprint formatting is:
xrayspx@pro:~$ echo "3b 1e fd 3a 66 ea 28 b1 66 97 39 47 03 a7 2c a3 40 a0 5b d5" | sed 's/ //g' | tr [:lower:] [:upper:]
3B1EFD3A66EA28B16697394703A72CA340A05BD5
At any rate, stupidly simple script:
@echo off
FOR /F "tokens=1" %%G IN (%1) DO (
FOR /F "tokens=1 USEBACKQ" %%F IN (`psexec.exe -nobanner \\%%G powershell.exe -Command "dir cert:LocalMachine\Root | findstr 3B1EFD3A66EA28B16697394703A72CA340A05BD5"`) DO (
echo %%G %%F >> tstout.txt
)
)
First, create a list of hosts to scan and save the file as hosts.txt or whatever.
run the scan with "certcheck.bat hosts.txt"
Your output will be in the "tstout.txt" file. That will output a space-separated list of hostnames + thumbprint if it exists on that host. If it doesn't it'll be blank. So you can "grep -v "3B1EFD3A66EA28B16697394703A72CA340A05BD5" tstout.txt" and get a list of hosts which don't have the cert installed.
- xrayspx's blog
- Log in to post comments
- 1516 reads

